COMPLIMENTARY
Cybersecurity Awareness Training (CAT)
Short, engaging videos to help your team recognize and avoid cyber threats, meet training requirements and strengthen your human firewall.

In 2024, attackers stole $2.2 billion by breaking into cryptocurrency platforms
The average heist was $14 million
Nearly 70% were from private key and seed phrase compromises
In February 2025, the single largest cryptocurrency hack in history occurred, causing $1.5 billion in losses




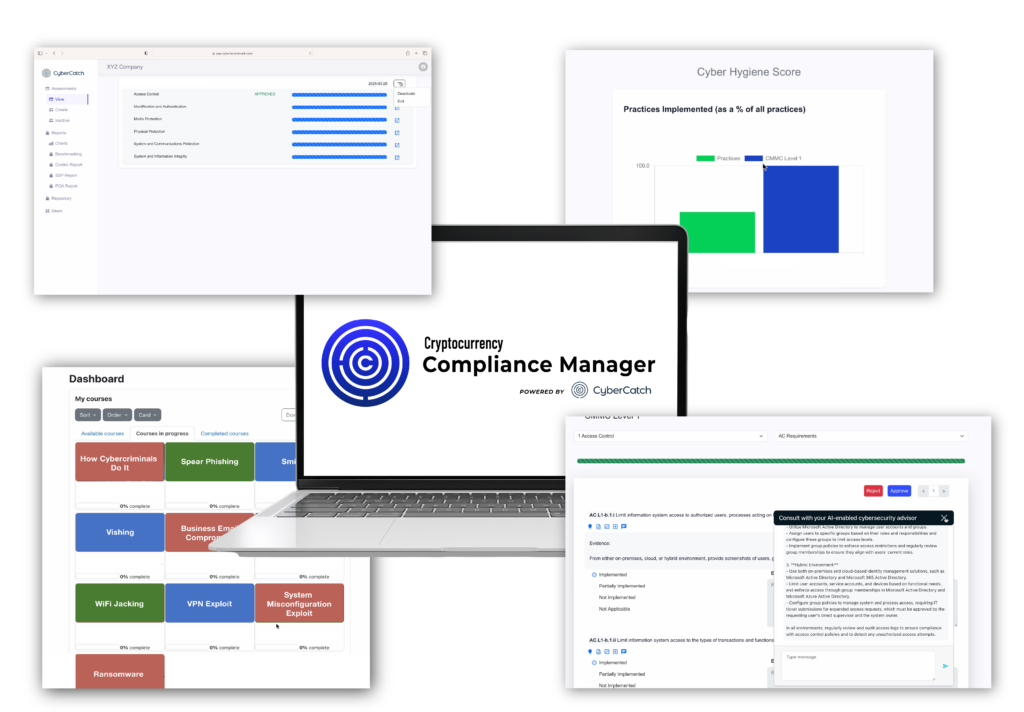


Simulation of a cyberattack using tactics, techniques and procedures (TTPs) currently being used by attackers targeting cryptocurrency platforms and companies to test controls and detect gaps and blind spots. Detailed report of findings and recommendations for immediate remediation and cyber risk mitigation.